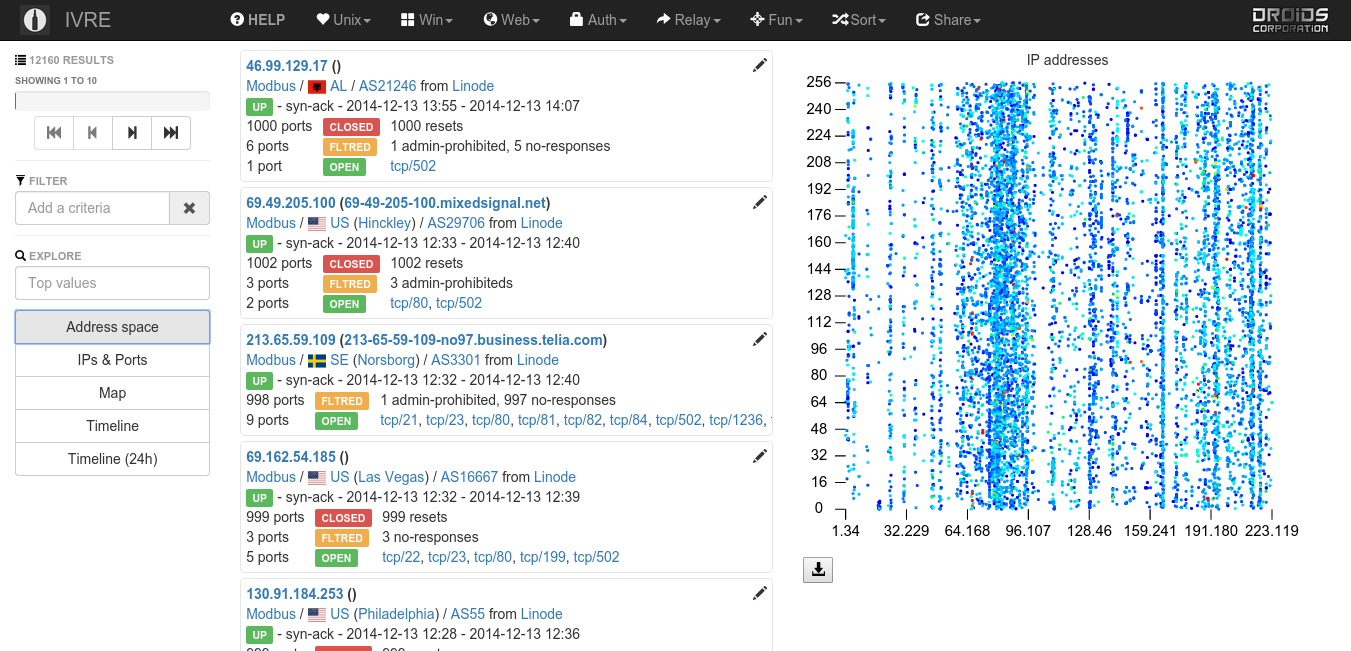
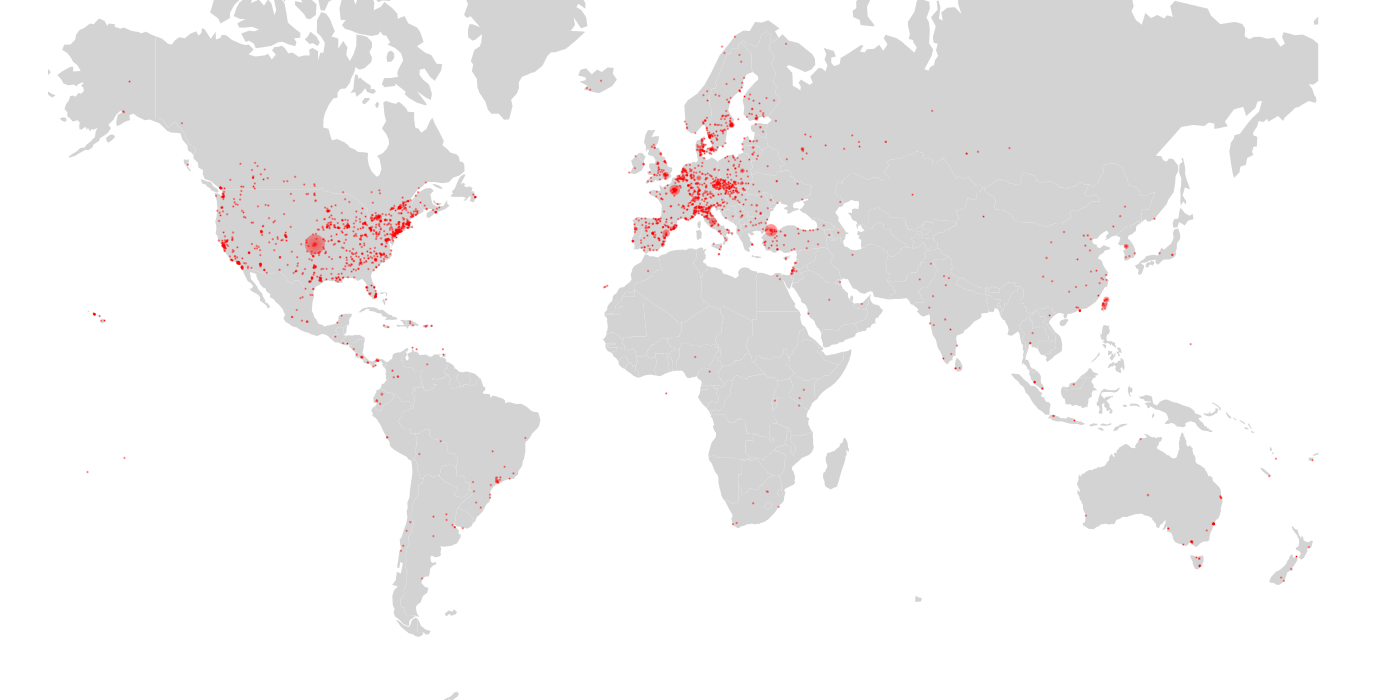
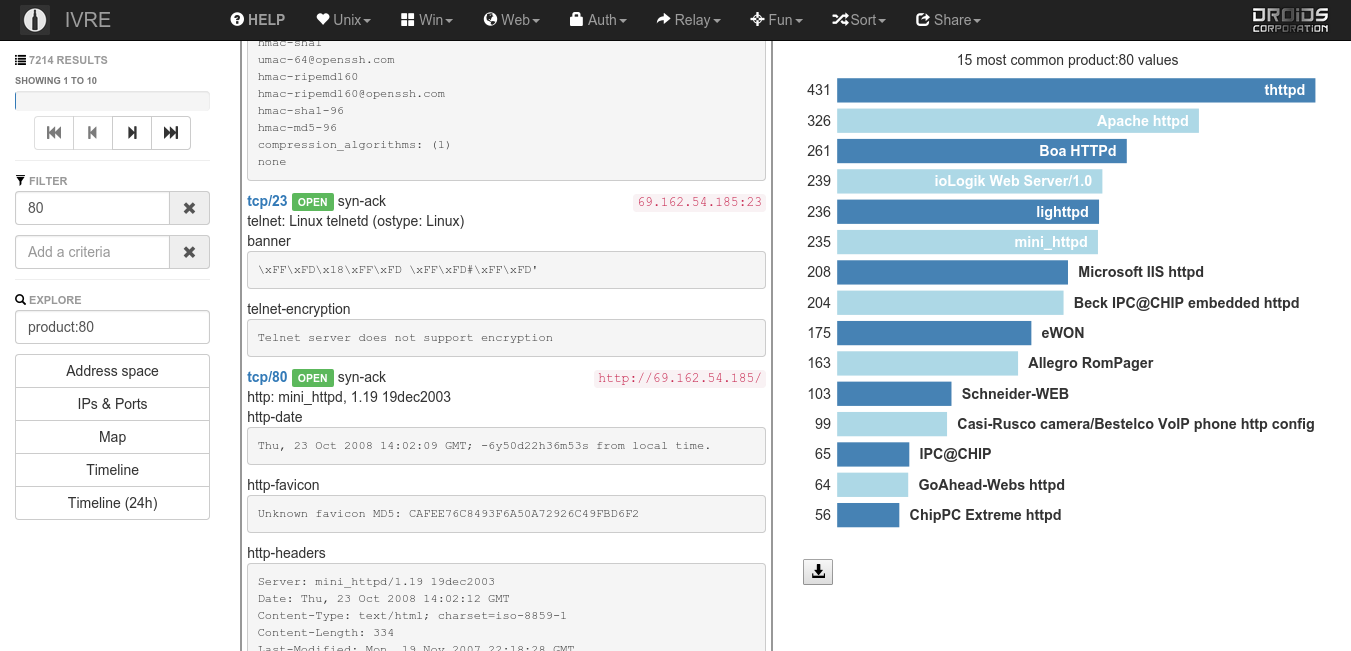
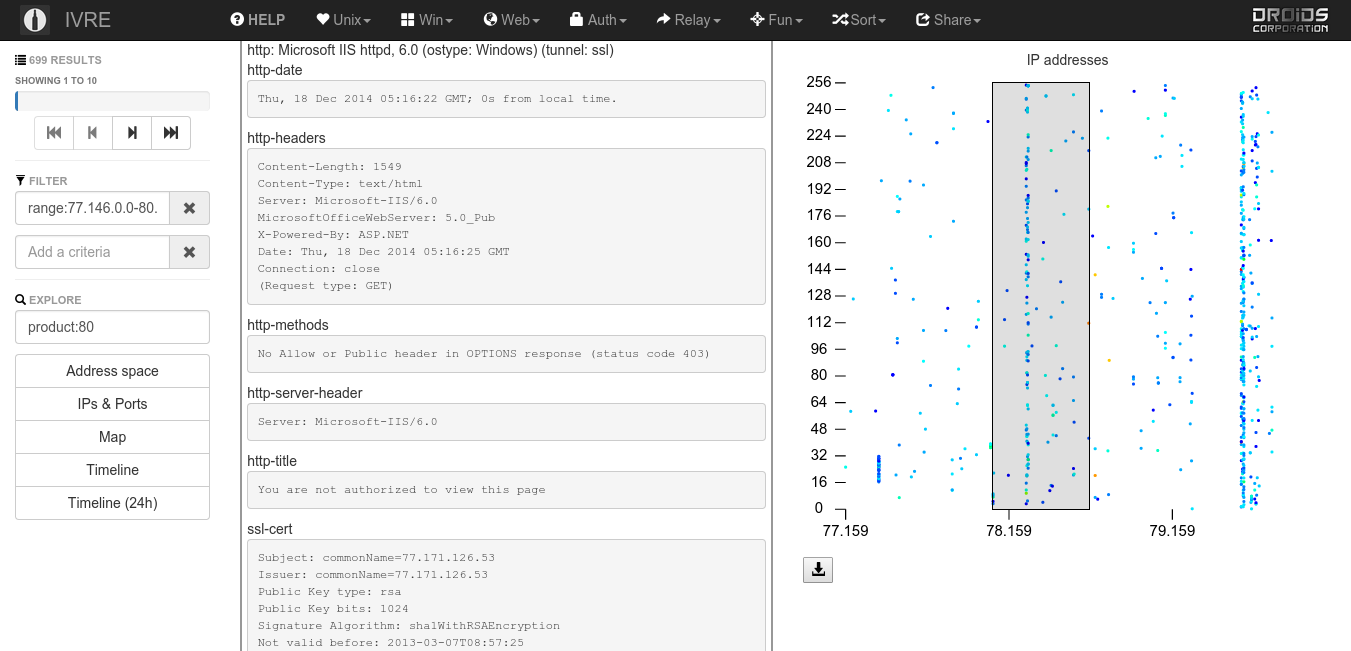
Get started
in no time.
There are several ways to install and deploy
IVRE; depending on your situation, you may want to use your
distribution packages (Kali Linux, Arch Linux or BlackArch
Linux users), Pip, Docker and Vagrant, or a manual
installation process.
On Kali Linux, just
run apt install ivre to install
the package. You
can also add ivre-doc if needed.
If you are
an Arch Linux user,
there is an
AUR
package, that should be easy
to install:
something like yay -S ivre ivre-web should work
(use yay -S ivre-git ivre-web-git to get the
current development version). If you use
BlackArch Linux, IVRE
should be installed and work out of the box. If not, just
run: pacman -S ivre ivre-web.
IVRE is also packaged
in Pypi, and you can
use Pip to
install it: pip install ivre.
Thanks to Docker
and Vagrant,
running IVRE is (almost) as easy as typing vagrant
up.
$ mkdir -m 1777 var_lib_mongodb ivre-share dokuwiki_data
$ wget -q https://ivre.rocks/Vagrantfile
$ vagrant up --no-parallel
Bringing machine 'ivredb' up with 'docker' provider...
Bringing machine 'ivreweb' up with 'docker' provider...
Bringing machine 'ivreclient' up with 'docker' provider...
[...]
$ docker attach ivreclient
root@e809cb41cb9a:/#
While
both AUR
and Pypi
packages are built for each
release, Docker
images are built automatically from the Github
repository and follow the development version, just
like AUR
ivre-git packages.
You don't want to use Docker, Archlinux or Pip? The
documentation
includes a
step-by-step installation procedure, that should be easy
to adapt to any Linux / Unix-like system.